Simple and Secure: An In-depth Analysis of the Matter Protocol's Security
[TAIWAN, 05th Sep. 2025]
SEALSQ is a European company dedicated to providing security solutions for IoT and industrial applications, with its primary products including Secure MCUs, PKI services, and Secure Elements. The company is also one of the few Matter-authorized non-VID scoped Product Attestation Authorities (PAAs).
We are very grateful to SEALSQ for providing us with this technical article on the Matter security mechanism. This article provides a clear and comprehensive introduction to the Matter protocol, detailing its operation and rigorous security measures. It covers the open-source connectivity standard, the end-to-end encryption system built on existing technologies like Wi-Fi and Bluetooth, and the simple, secure process for onboarding new devices. The article also elaborates on Matter's Public Key Infrastructure (PKI) architecture, specifically the chain of trust among the Product Attestation Authority (PAA), Product Attestation Intermediate (PAI), and Device Attestation Certificate (DAC), which is crucial for verifying the authenticity of Matter devices.
Introduction
The Matter protocol is an open-source connectivity standard designed to make it easier for smart home devices to work together. Matter specification is defined by CSA (Connectivity Standards Alliance) which major companies in the technology industry have joined, including Apple, Amazon, Google, and the Zigbee Alliance…etc.
The goal of the Matter protocol is to create a unified standard for smart home devices, a more connected, interoperable, and secure smart home ecosystem for users. Therefore, users can simplify the process of setting up and managing smart home devices from different smart home vendors.
It is worth noting that Matter is built on existing technologies such as Wi-Fi, Bluetooth Low Energy (BLE), and Thread, and relies on a secure, end-to-end encryption system to protect user data. The protocol also offers a simple and secure onboarding process for new devices, enabling seamless integration. This dual focus allows Matter to simultaneously meet the two key demands of smart home devices: security and convenience.
Matter Security
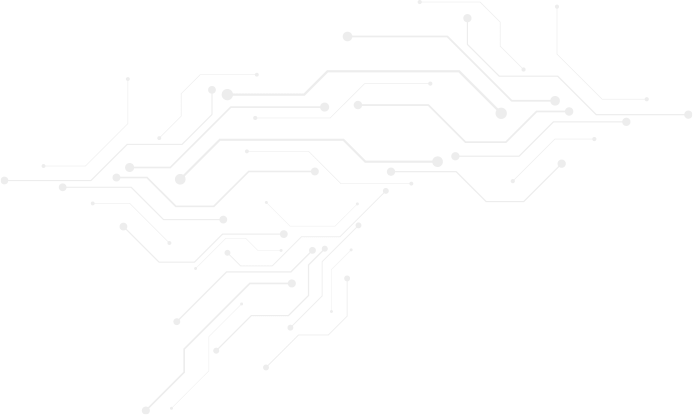
First, you may refer to Figure 1 for an overview of how Matter’s security mechanism operates. In order to provide a more in-depth introduction to the operation of Matter, some technical terms are explained as follows:
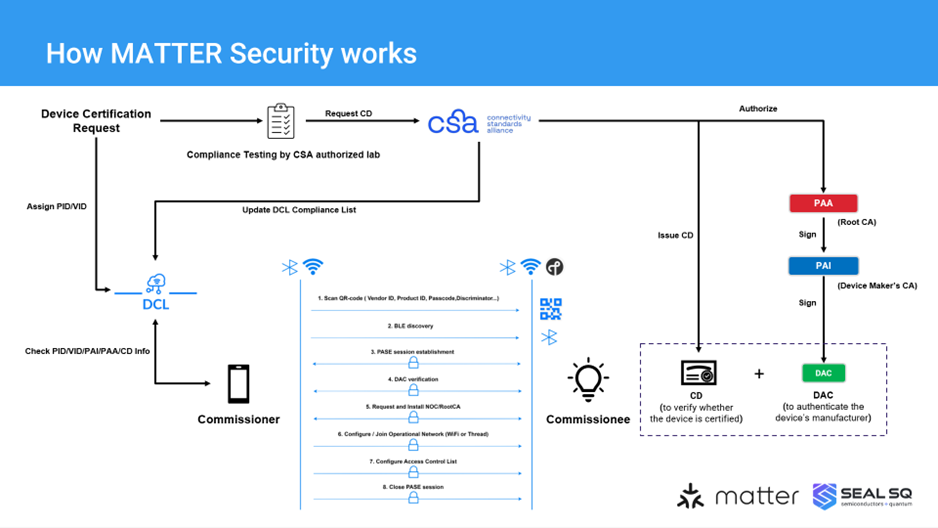
Figure 1. How Matter security works
Node: An addressable entity that supports the Matter protocol stack and (once Commissioned) has its own Operational Node ID and Node Operational credentials. A device may host multiple Nodes.
Fabric: A logical collection of communicating Nodes, sharing a common root of trust, and a common distributed configuration state.
Commissionee: An entity, a new device, that is being commissioned to become a Node that will be added/commissioned to a Fabric.
Commissioner: A role of a Node that performs Commissioning for adding new devices to the Fabric. The commissioning will be done by a smartphone which is in themselves Nodes of the Fabric.
Administrator: A Node having Administer privilege over another Node.
Product Attestation Authority (PAA): An entity that operates a root-level Certificate Authority for the purpose of Device Attestation.
Product Attestation Intermediate (PAI): An entity that operates an intermediate-level Certificate Authority for the purpose of Device Attestation.
Device Attestation Certificate (DAC): An RFC 5280 compliant X.509 v3 document with attestable attributes.
Certification Declaration (CD): A digitally signed token that conveys Matter certification status of a vendor’s certified Device. Device vendors need to apply it from CSA.
Vendor ID (VID): A 16-bit number that uniquely identifies the Vendor of the Device. Device vendors need to apply it from CSA.
Product ID (PID): A 16-bit number that identifies the type of a Device, uniquely among the product types made by a given vendor. Device vendors need to apply it from CSA.
Node Operational Certificate (NOC): The NOC consists of the Root CA (acting as Fabric’s trust anchor) and a Node unique certificate and private key. The Root CA will be used by the Commissioner to authenticate after commissioning has ended. The NOC and private key are used for communication between different Fabric Nodes.
Distributed Compliance Ledger (DCL): The DCL is a secure distributed point of device metadata and Product Attestation Authorities (PAA) certificates. It’s used for tracking certification status and vendor-maintained information such as product name, product description and upgrade firmware URL …etc.
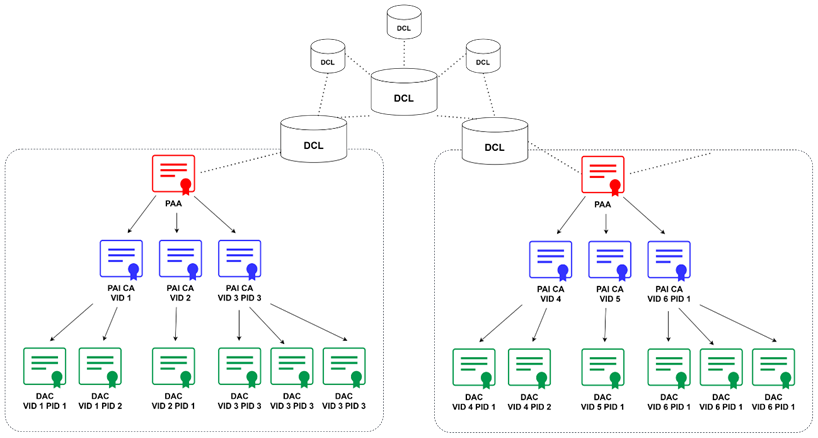
Figure 2. The PKI hierarchy of Device Attestation of Matter with DCL
Device attestation & PKI
The device attestation provides mechanisms for Commissioners and Administrators to determine whether a Node is a genuine certified product before sharing sensitive information such as keys and other credentials. The device attestation feature relies on a Device Attestation Certificate (DAC) chain and on a Certification Declaration (CD).
All commissionable Matter Nodes SHALL include a Device Attestation Certificate (DAC) and corresponding private key, unique to that Device. The DAC is used in the Device Attestation process, as part of Commissioning a Commissionee into a Fabric. The DAC SHALL be issued by a Product Attestation Intermediate (PAI) that chains directly to an approved Product Attestation Authority (PAA).
The DAC also SHALL contain specific values of Vendor and Product ID in its subject field to indicate the vendor and product type of the specific node. The validity period of a DAC is determined by the vendor and MAY be set to the maximum allowed value to indicate that the DAC has no well-defined expiration date.
The Device Attestation PKI hierarchy consists of the PAA, PAI and individual DAC. The public key from the associated PAI certificate is used to cryptographically verify the DAC signature. The PAI certificate in turn is signed and attested to by the Product Attestation Authority (PAA) CA. The public key from the associated PAA certificate is used to cryptographically verify the PAI certificate signature. The PAA certificate is an implicitly trusted self-signed root certificate. In this way, the DAC chains up to the PAI certificate, which in turn chains up to the PAA root certificate.
Figure 3. The PKI hierarchy of Matter DAC
Commissioners SHALL use PAA and PAI certificates to verify the authenticity of a Commissionee before proceeding with the rest of the Commissioning flow.
Workflow of device commissioning
Device commissioning is the process of joining a node to a Fabric and establishing a secure PASE (Passcode-Authenticated Session Establishment) session using a shared passcode with a PAKE (Password-Authenticated Key Exchange) protocol is required and defined in Matter specification.
During the PASE session, verifying the DAC of Matter smart home device is also a mandatory process. The below figure illustrates the workflow of commissioning a new Matter smart home device.
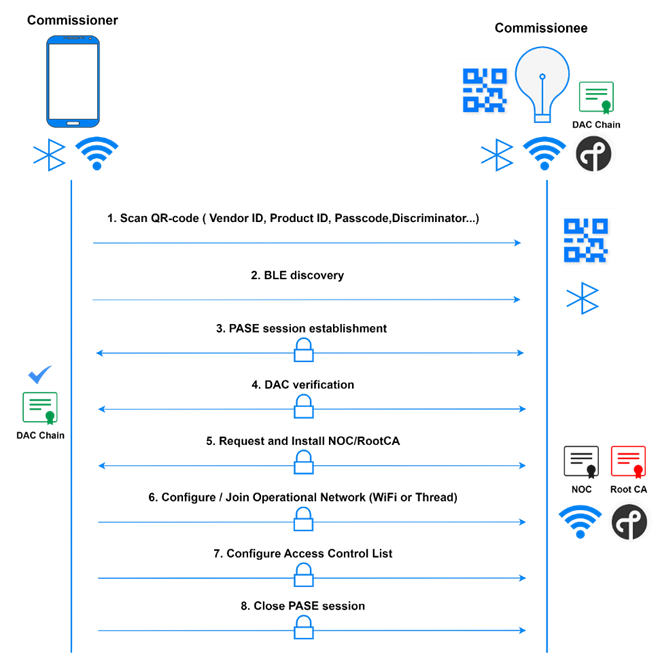
Figure 4. The workflow of commissioning a new Matter smart home device
The Commissioner scans the QR-Code on the device to get all the needed information to set up the Commissionee into commissioning mode. This QR-Code contains base38 encoded binary including the Version, Vendor ID, Product ID, Passcode…etc.
Once the Commissionee is in commissioning mode, the Commissioner will start a Bluetooth Low Energy scan to find the Commissionee. Starting from this step, the PASE session between the Commissioner and the Commissionee will be established and secured based on the PAKE protocol and deriving the encryption key by key derivation function (PBKDF) from the passcode that the Commissioner obtained from QR-code.
The Commissioner requests a Device Attestation Certificate (DAC) chain and the Certification Declaration (CD) from the Commissionee. Since the DAC is a certificate chain that chains up to a root certificate Product Attestation Authority (PAA), the Commissioner will verify if the PAA is verified and managed by the CSA and if the CD, which is provided by the CSA as part of the Product Certification process, contains the needed information of DAC for verification.
Following the Device Attestation Procedure and the Commissionee is verified, the Commissioner will request operational Certificate Signing Request (CSR) from the Commissionee using the CSRRequest command in order to generate the NOC for the Commissionee and the Commissioner will install the NOC on the Commissionee using the AddTrustedRootCertificate and AddNOC commands.
The Commissioner configures the operational network at the Commissionee using commands such as AddOrUpdateWiFiNetwork or AddOrUpdateThreadNetwork.
The Commissioner configures the Access Control List on the Commissionee in any way it sees fit. The ACL will include information about the Fabric, privilege level, authentication mode, subjects…etc. The commissioning process is completed and the Commissioner closes the PASE session and BLE session.
From the above explanation, it can be seen that the MATTER security mechanism is highly rigorous and also bears some similarities to the HomeKit security architecture:
1. A complete device attestation chain is established from the PAA, through the PAI, down to the DAC.
2. Devices must be tested and verified by a CSA-authorized laboratory before they can become MATTER-certified devices.
3. Only after MATTER devices mutually verify their authenticity can they establish an encrypted channel for communication.
In practice, MATTER can simultaneously meet the dual demands of smart home devices for security and convenience. However, device vendors also need to invest sufficient resources—for example, joining the CSA as a member, establishing a PAI to issue DACs, integrating wireless SoCs or chips, testing various MATTER application interfaces, submitting products for certification, and adjusting production test programs. For interested manufacturers, apart from exploring and overcoming these challenges on their own, they may also consult with ARAD Technology or SEALSQ TW (CSA-authorized PAA service provider) for turnkey solutions.
SEALSQ (NASDAQ: LAES) is a European firm that primarily provides Secure MCUs, PKI services, and Secure Elements, delivering security solutions for IoT and industrial applications. SEALSQ is one of the Matter-authorized non-VID scoped PAAs, which means it can provide managed PKI services for smart home device manufacturers, enabling them to manage their own PAI — either remotely or through offline ways — while binding them to their unique VID. Once the PAI has been established, device manufacturers can easily access it via SEALSQ’s INeS web platform and begin issuing DACs for each of their smart home devices.
SEALSQ official website & TAIWAN contact: https://www.aradconn.com/purchase/MatterPAA/
Image and Text Copyright Statement:
This article is published with the authorization of SEALSQ TW.
All text and image content in this article (including but not limited to headings, body text, analysis, and summaries) are the copyright of SEALSQ TW. Any form of reproduction, reprinting, modification, or commercial use without written authorization is strictly prohibited.
📢 Get Ready for Our Latest Episode of BLE Tech Pulse Decoded on Aradtube!
Subscribe to our channel and hit that notification bell so you don't miss our newest video releases.
🔗 YouTube: https://www.youtube.com/@Aradconn
Edited by Intl. Commercial Development Manager: Mr. Tim Chien